Why Twitter is asking to change your password?
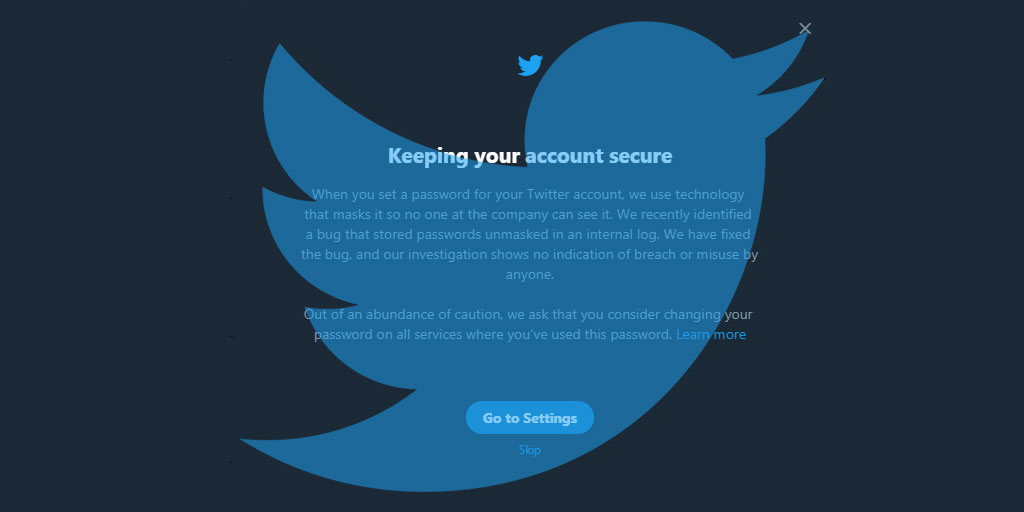
Yesterday on 3rd of May The official Twitter support handle posted tweets asking everyone to change their Twitter account passwords. It referenced to a blog published by twitter CTO Parag […]

Yesterday on 3rd of May The official Twitter support handle posted tweets asking everyone to change their Twitter account passwords. It referenced to a blog published by twitter CTO Parag […]

As the digital transactions are growing, everyone started having banking Applications on their smartphone. These apps provide ease in performing transactions and other bank related tasks. But beware, there is […]

We do surf and visit a lot of websites every day and we come across this term HTTPS frequently. Many of the websites, especially the popular ones have this special […]

Ransomware…! The thing hitting the news these days. Almost a month ago, half of the world was hit by the dirty WannaCry and now it’s the time of Petya. Petya […]

Website defacement is an attack on a website that changes the visual appearance of the site or a webpage. Defacement is generally used to spread messages by politically motivated “cyber protesters” […]

Targeted cyber attacks are those which are performed over a period of time with a clear intention of damaging an organization’s reputation by stealing data from their network and servers. […]

A very crucial and highly targeted sector by hackers is banking. Banks are the place where a country’s money lies. Almost all the banks going digital now a days, opened […]

The end of the year is already upon us. It is that time of the year, when we look back at last 12 months and remember all the events happened […]

Data Theft or Data Breach, as quoted by TechTarget is an incident in which sensitive, protected or confidential data has potentially been viewed, stolen or used by an individual unauthorized […]

“Ransomware is more about manipulating vulnerabilities in human psychology than the adversary’s technological sophistication” — James Scott, Sr. Fellow, Institute for Critical Infrastructure Technology According to Yahoo’s latest revelation, two years […]